
The WhatsApp Lawsuit and a Tangent on What's Technically Possible
A class-action lawsuit claims Meta can access WhatsApp messages. I don’t know if it’s true. But the lawsuit gave me a reason to revisit a technical capability I’ve been writing about.

A class-action lawsuit claims Meta can access WhatsApp messages. I don’t know if it’s true. But the lawsuit gave me a reason to revisit a technical capability I’ve been writing about.

Companies can already mine your non-encrypted data on their servers. It’s your end-to-end encrypted data that was supposed to be untouchable. On-device ML first changed that, turning your own phone into the profiling engine that encryption was meant to prevent. On-device LLMs now take that to another level.

This article examines how our increasingly intimate relationships with AI create a dangerous asymmetry, where humans trust AI companions that may soon be executing hidden agendas. Vishal, an AI industry veteran, warns that this dynamic makes us highly susceptible to manipulation, moving beyond simple influence to the ‘inception’ of ideas we could end up believing are our own.
End-to-end encryption isn’t enough. Learn how on-device machine learning models can silently profile you—and how to fight back.
I loved the em dash for its messy elegance. Now it just makes my writing look like it was spat out by a language model.
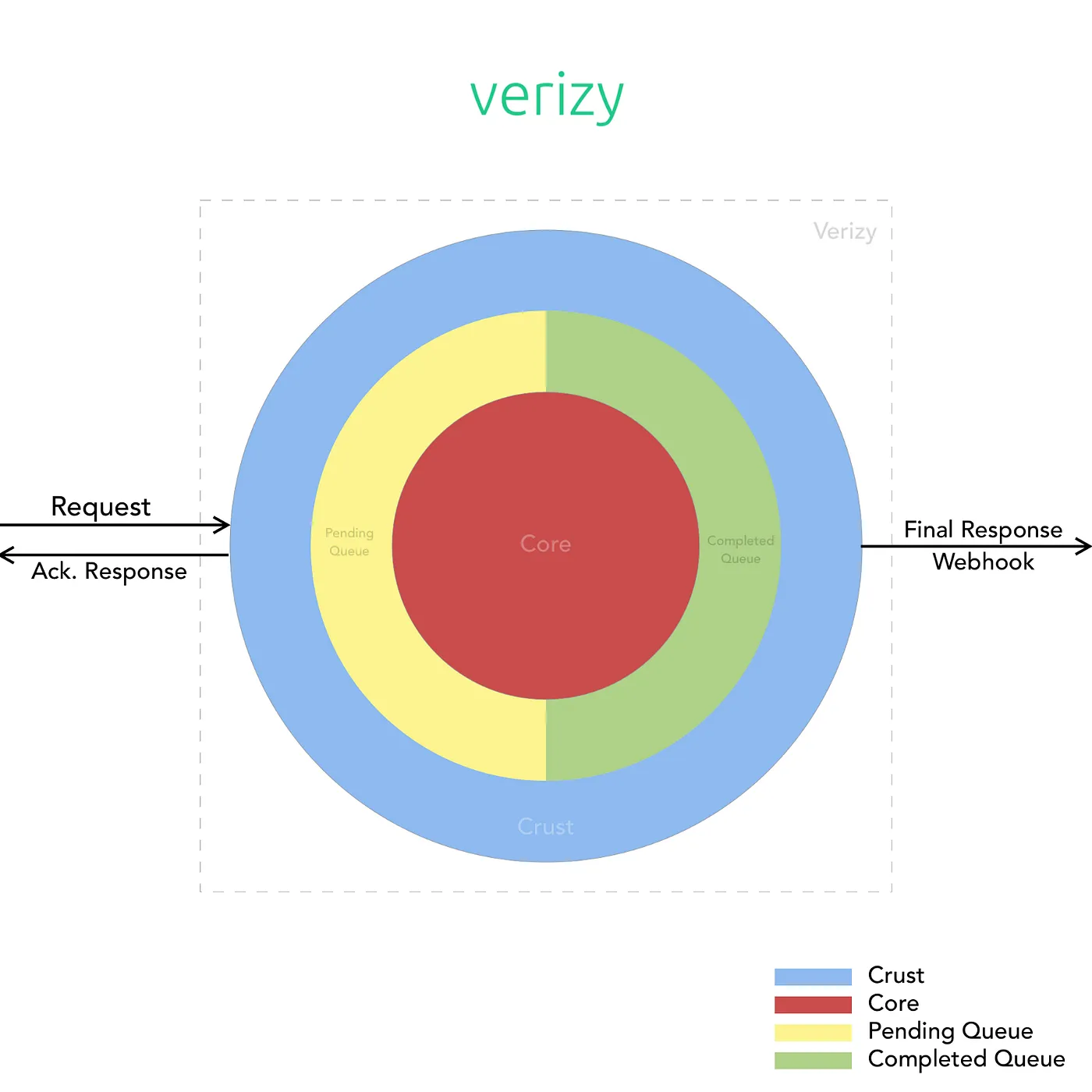
Verizy efficiently processes over 1 million complex monthly requests using a dual-service infrastructure called Crust and Core, handling customer interactions and intensive data processing respectively, ensuring 100% uptime in 6 months with auto-scaling, load-balancing, and continuous updates. This architecture guarantees no request loss and maintains high performance and reliability.