Update: March 2025
I wrote the main article in 2023. Based on my anecdotal observations, since the second half of 2024 the Secure ID checkbox is no longer automatically checked by Juspay—I’ve confirmed this on both CRED and Swiggy. That’s a welcome development. Below is my original, unmodified post.
What I’ve Observed
When I use net banking to pay for my orders on apps like Swiggy and CRED (not an exhaustive list), they use an intermediary called Juspay (among others) to process these payments. Juspay, as per their website, provide an end-to-end payment stack that apps that require payments from their users may use to enable various payment methods (cards, net banking, UPI, BNPL, etc.) with a single integration of Juspay.
When using net banking on apps that use Juspay, I have noticed that Juspay does something seemingly-trivial, which I think is a risky security practice. Juspay automatically checks an anti-phishing measure used by some banks like HDFC, which is supposed to be verified and checked by the user.
HDFC Bank has something called a ‘Secure Access ID’ (also called ‘Authentication Image’ and ‘Authentication Message’ in a different place—bad messaging, HDFC) which is a combination of an image and a text message that the user chooses when setting up their credentials on HDFC net banking site. This is shown to the user during login (after entering their username) which she is then supposed to confirm before entering the password and proceeding with the login.
This is a typical HDFC login page displayed on a mobile screen during a payment flow that does not involve Juspay. Note that I have masked my actual details and overlaid them with gray boxes.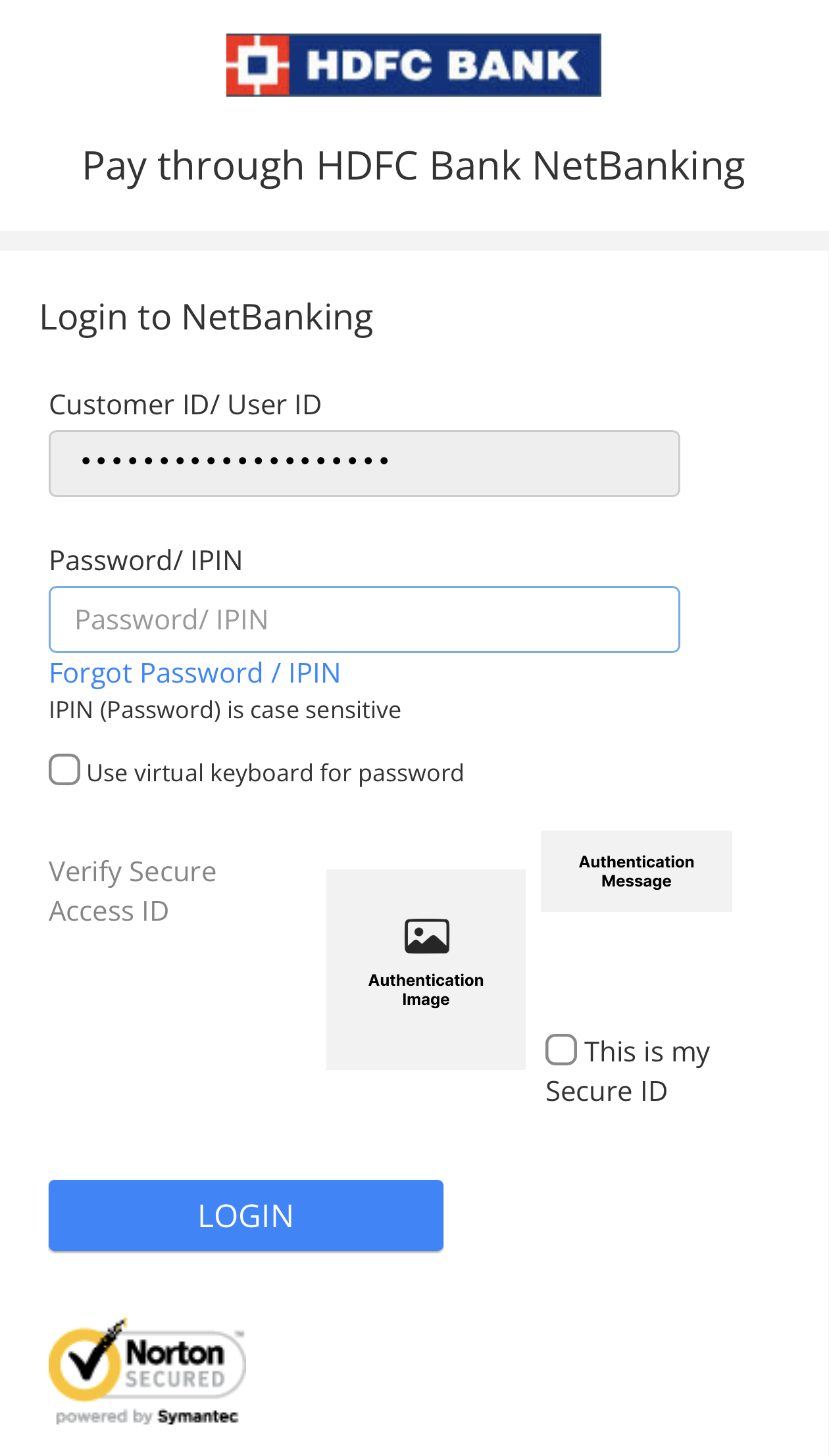
This is done to possibly mitigate their users from phishing attacks. Some details on how that works—since the authentication image and message are negotiated between the user and HDFC Bank’s server during account setup, when the same image and message are shown during a login attempt, they act as an identification to the user that they are entering their credentials on the valid HDFC site and not a malicious site that is posing as HDFC Bank to collect your credentials. A malicious party could create a site that looks just like HDFC Bank’s, but ideally cannot know every individual user’s Authentication Image and Message without gaining access to the bank’s servers. Hence, when a user is about to log in to the HDFC Bank site, verifying their Authentication Image and Message and then checking the box next to “This is my Secure ID” is imperative. HDFC Bank has been instructing and training its users to check this every time by leaving the box unchecked. The login does not proceed without checking this box. This way, the user makes a deliberate action of checking it, improving the chances of them verifying their Secure ID details, as opposed to leaving it checked by default, where the user would learn to stop noticing and verifying the Secure ID details.
When the HDFC net banking site is served through Juspay, they check this box next to “This is my Secure ID” by default before you land on the page, defeating its whole purpose. Eventually, if a user regularly uses HDFC net banking on Swiggy or similar, they would be trained not to pay attention to the Secure ID details, increasing the risk of a phishing attack.
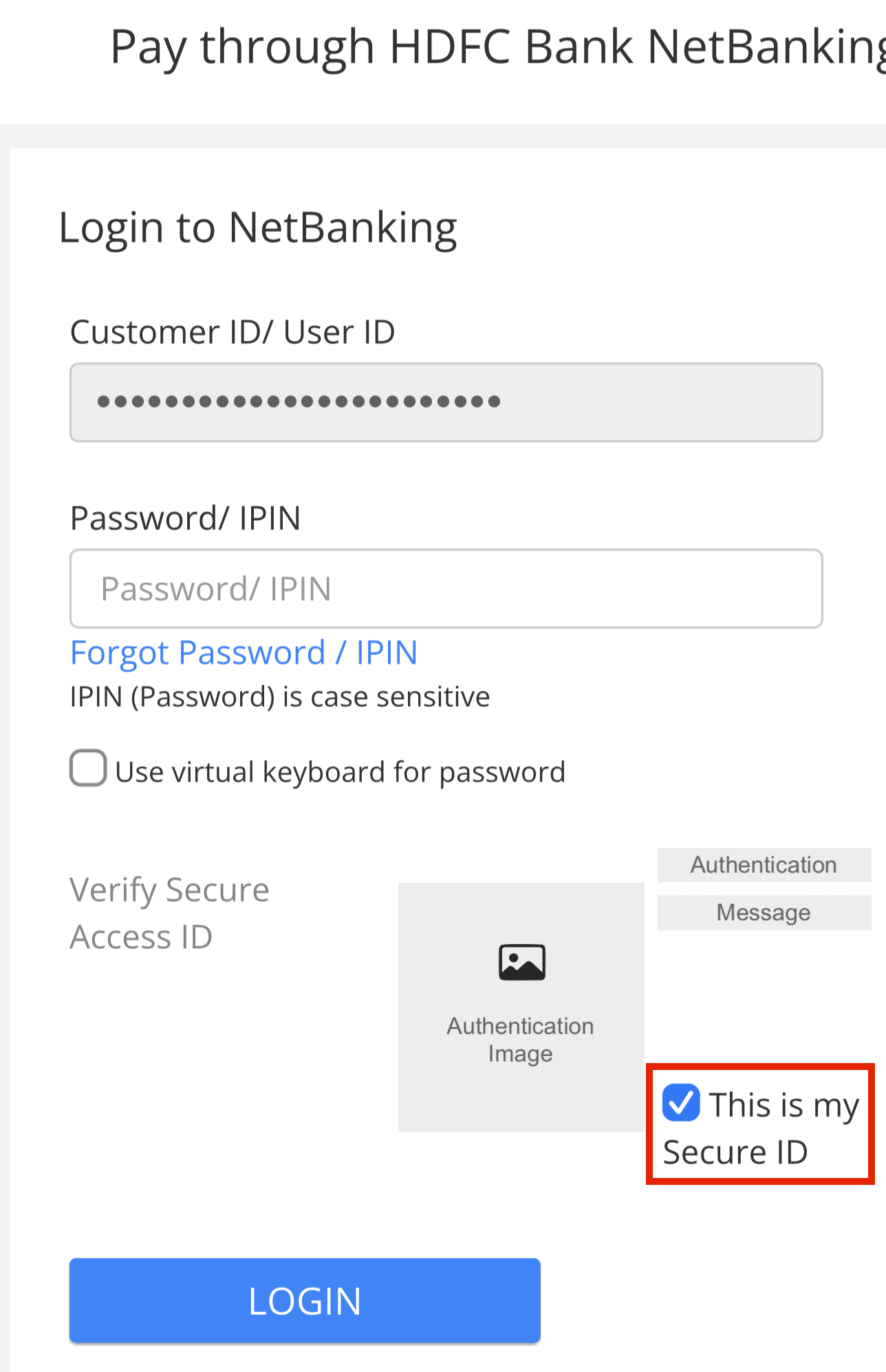
HDFC Bank login page when going through Juspay on Swiggy. Notice how ‘This is my Secure ID’ is checked by default.
I want to acknowledge that this, by itself, would not open the user up to attacks significantly. But the cybersecurity domain works on the principles of defining a Threat Model and designing mitigations for each threat that comes under the model. Whether HDFC Bank did a great job at designing their threat model is not for me to decide. But, a private party (Juspay), who is not HDFC Bank, making these changes to the HDFC Bank site behavior is this party modifying the bank’s Threat Model. Since Juspay is used on a decent number of largely-used platforms in India, this has the potential of modifying user behavior towards less-secure practices.
What is a Phishing Attack?
Phishing is a cyberattack designed by a malicious party who pretends to be a trustworthy entity in order to steal and gain access to sensitive information like credentials (username and password), payment details (credit cards), bank account numbers, and other data of unsuspecting users.
Generally, a phishing attack involves using inconspicuous and fraudulent emails, websites, text messages, or phone calls that look and feel innocent. Acting on these could trick the user into giving up their sensitive details or downloading a malware.
A successful phishing attack could lead to financial losses, credit card fraud, identity theft, ransomware attacks, or data breaches.
Example of an Attack
- You receive an email from “HDFC Bank Ltd.”
- The email says that you have a compelling reward on your debit card that you may avail by logging in with the link provided.
- The link reads https://debit-card-offer.rewards.hdfcbenk.com/email-offer-rs-10000, or it is hidden behind a “Log In to Avail” button.
- The email looks legitimate—the branding, the words used, layout, etc. all match how HDFC Bank’s emails usually are.
- You do not notice that the domain reads ‘hdfcbenk.com’ instead of ‘hdfcbank.com’ and click on it.
- Your browser opens up with a site that looks exactly like the HDFC Bank site that you’re used to.
- You enter your credentials as usual, but now your credentials are in the hands of the malicious party as they own and control the site.
- Post this one of two things could happen—they either fail the login attempt, saying the service is done and to check back later.
- Or, a more complex attack could mirror your credentials to the actual HDFC site and proceed to log in from the malicious party’s end if they have further steps they want your involvement for before the attack ends.
- Either way, your credentials are in the hands of a malicious party.
How Big a Deal is this?
In my opinion, the biggest issue here is a third party modifying the threat model mitigations undertaken on a bank’s website.
The automatic checking of the anti-phishing measure alone doesn’t expose the user to a huge attack. But, apps like Swiggy are sometimes used every day, and it’s easy for a user to look past the anti-phishing message after using net banking through Juspay enough number of times.
This would eventually lead to an attack as explained above being more plausible, as the user is used to not paying attention to the anti-phishing measure.
Other sites like ICICI Bank don’t even use an anti-phishing measure as HDFC Bank, so how big a deal can this be? Probably not a huge one, in comparison. But I cannot be the judge of that, I do not have the data these banks have about how their users are usually targeted, nor do I have the exact reasons for their threat model definitions.
I believe that no third party, like Juspay, should be making that judgement.
Another Observation
I don’t want this post to concretely say that HDFC’s security practices are superior. While I was playing around with their site through and without Juspay, I was able to change the username/Customer ID during login, which is just an 8-digit number that I tried incrementing and decrementing from mine and view other customers’ Authentication Images and Messages.
A more complex phishing attack could potentially create a fake site that looks like HDFC’s, collect the Customer ID first, pass it through HDFC Bank’s real site, obtain the actual Authentication Message and Image, send it back to the fake site to have the victim of the attack even pass the anti-phishing measure.
I do not know how advanced HDFC’s measures to avoid robotic access to their site are, but it cannot be fool-proof when I was able to view other people’s sometimes-funny Authentication Messages within minutes of playing around on their site.
Conclusion
Given all this, you may view HDFC’s anti-phishing measure as being pointless, and what Juspay does be alright, but the issue remains—the only entity who can determine this should be HDFC or someone auditing HDFC’s sites, a third party such as Juspay should not modify the site’s behavior.
Disclaimer
I am writing this as someone from the outside, without having the entire view into HDFC’s security practices and by assuming that Juspay checks the Secure ID confirmation box by default without consulting with HDFC. I made that assumption because the behaviors are different between the HDFC site and HDFC site through Juspay.
This post does not tell the entire story, rather just states an observation I made and discusses its potential issues from my limited perception as an outsider.
Do not consider this a well-rounded cybersecurity advice.
tl;dr
This blog post examines how Juspay’s auto-checking of HDFC Bank’s anti-phishing ‘Secure Access ID’ could undermine user security. I argue that this action, while not immediately dangerous, could condition users to be less vigilant against phishing attacks. The post contends that third parties like Juspay should not alter a bank’s security measures. The post also questions if HDFC’s anti-phishing measure is effective, in the first place and discusses who should be responsible in defining and mitigating a site’s threat model.
